Raise Errors from Rules
The End of Life (EOL) date of Rules and Hooks will be November 18, 2026, and they are no longer available to new tenants created as of October 16, 2023. Existing tenants with active Hooks will retain Hooks product access through end of life.We highly recommend that you use Actions to extend Auth0. With Actions, you have access to rich type information, inline documentation, and public
npm packages, and can connect external integrations that enhance your overall extensibility experience. To learn more about what Actions offer, read Understand How Auth0 Actions Work.To help with your migration, we offer guides that will help you migrate from Rules to Actions and migrate from Hooks to Actions. We also have a dedicated Move to Actions page that highlights feature comparisons, an Actions demo, and other resources to help you on your migration journey.To read more about the Rules and Hooks deprecation, read our blog post: Preparing for Rules and Hooks End of Life.error and error_description result values.
Suppose your callback URL is https://travel0.com/callback and you’re using the standard query response mode. You would receive this response:
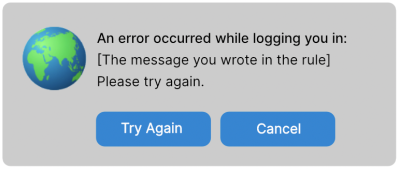
Retry login after a rule error
A likely next step is to request a new authorization. However, in most cases, Auth0 already knows who the user is and so doesn’t ask for login information. Instead, rules run immediately and the rule denies authorization again. This can become an endless loop. The user needs an opportunity to provide new credentials. There are two ways your app can make the login page display again:-
Add a directive in the request to force the display of the login page:
- Use a
prompt=loginparameter to an OIDC/OAuth2 request. - Use a
ForceAuthn="true"attribute in a SAML request.
- Use a
- Log the user out of Auth0 before you send a new request.

