Secure Google Cloud Endpoints with Auth0
Google Cloud Endpoints (GCE) is an API management system providing features to help you create, maintain, and secure your APIs. GCE uses OpenAPI to define your API’s endpoints, input and output, errors, and security description.
For more information on the OpenAPI spec, see the OpenAPI Specification repository on GitHub.
This tutorial will cover how to secure Google Cloud Endpoints with Auth0.
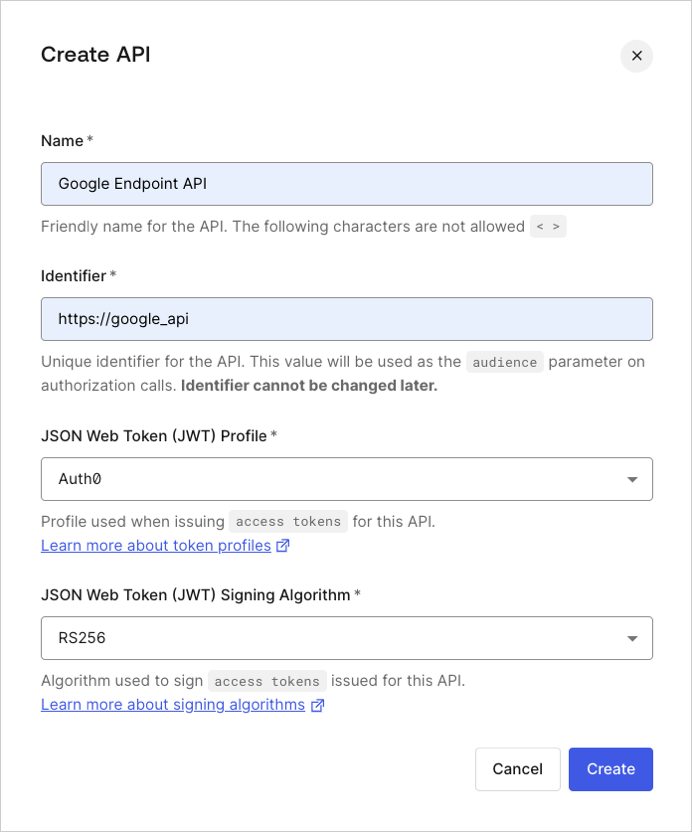 Make note of the API identifier (
Make note of the API identifier (
In the above example, the
You’ll get the following response:
Which is exactly what we want!
Now go to the Test page of your Google Endpoints API definition on the Auth0 Dashboard, and copy the under the Response:
Perform a
And that’s it!
Prerequisites
Before you begin you’ll need a deployed GCE API. If you haven’t already created an API, complete the Cloud Endpoints Quickstart located in Google documentation. The quickstart will walk you through creating a simple GCE API with a single endpoint,/airportName, that returns the name of an airport from its three-letter IATA code.
Define the API in Auth0
Go to Auth0 Dashboard > Applications > APIs, and create a new API.
http://google_api in the screenshot above) to use in the following step.
Update the API Configuration
Next, we’ll update the OpenAPI configuration file for the GCE API. For the sample API created during the quickstart this file isopenapi.yaml.
Add Security Definitions
Open the configuration file and add a newsecurityDefinitions section. In this section, add a new definition (auth0_jwt) with the following fields:
| Field | Description |
|---|---|
authorizationUrl | The authorization URL, should be set to “https:///authorize” |
flow | The flow used by the OAuth2 security scheme. Valid values are “implicit”, “password”, “application” or “accessCode”. |
type | The type of the security scheme. Valid values are “basic”, “apiKey” or “oauth2” |
x-google-issuer | The issuer of a credential, should be set to “https:///“ |
x-google-jwks_uri | The URI of the public key set to validate the signature. Set this to "https://\{yourDomain}/.well-known/jwks.json" |
x-google-audiences | The API’s identifier, make sure this value matches what you defined on the Auth0 dashboard for the API. |
Update the Endpoint
Now, update the endpoint by adding asecurity field with the securityDefinition we created in the previous step.
security field tells the GCE proxy that our /airportName path expects to be secured with the auth0-jwt definition.
After updating the OpenAPI configuration, it should look something like this:
Redeploy the API
Next, redeploy your GCE API to apply the configuration changes. If you followed along with the Cloud Endpoints Quickstart you can redeploy by entering the following in Google’s Cloud Shell:Test the API
Once you’ve redeployed, call the API again with no security.GET request to your API with an Authorization Header of Bearer {ACCESS_TOKEN} to obtain authorized access:

