Connect to OpenID Connect Identity Provider
Prerequisites
-
Register your Application with Auth0.
- Select an appropriate Application Type.
- Add an Allowed Callback URL of
{https://yourApp/callback}. - Make sure your Application’s Grant Types include the appropriate flows.
Steps
To connect your application to an OIDC , you must:- Set up your app in the OpenID Connect Identity Provider
- Create an enterprise connection in Auth0
- Enable the enterprise connection for your Auth0 Application
- Test the connection
Set up your app in the OpenID Connect Identity Provider
To allow users to log in using an OIDC Identity Provider, you must register your application with the IdP. The process of doing this varies depending on the OIDC Identity Provider, so you will need to follow your IdP’s documentation to complete this task. Generally, you will want to make sure that at some point you enter your callback URL:https://{yourDomain}/login/callback.
Find your Auth0 domain name for redirects
If your Auth0 domain name is not shown above and you are not using our custom domains feature, your domain name is a concatenation of your tenant name, your regional subdomain, and
auth0.com, separated by the dot (.) symbol.For example, if your tenant name is exampleco-enterprises, and your tenant is in the US region, your Auth0 domain name would be exampleco-enterprises.us.auth0.com and your Redirect URI would be https://exampleco-enterprises.us.auth0.com/login/callback.However, if your tenant is in the US region and was created before June 2020, then your Auth0 domain name would be exampleco-enterprises.auth0.com and your Redirect URI would be https://exampleco-enterprises.auth0.com/login/callback.If you are using custom domains, your Redirect URI would be https://<YOUR CUSTOM DOMAIN>/login/callback.Create an enterprise connection in Auth0
Before you configure a OIDC Enterprise Connection in Auth0, ensure you have the Application (client) ID and the generated when you set up your app in the OIDC provider.Create an enterprise connection using the Auth0 Dashboard
To be configurable through the Auth0 Dashboard, the OpenID Connect (OIDC) Identity Provider (IdP) needs to support OIDC Discovery. Otherwise, you can configure the connection using the Management API.
-
Navigate to Auth0 Dashboard > Authentication > Enterprise, locate Open ID Connect, and click its
+.
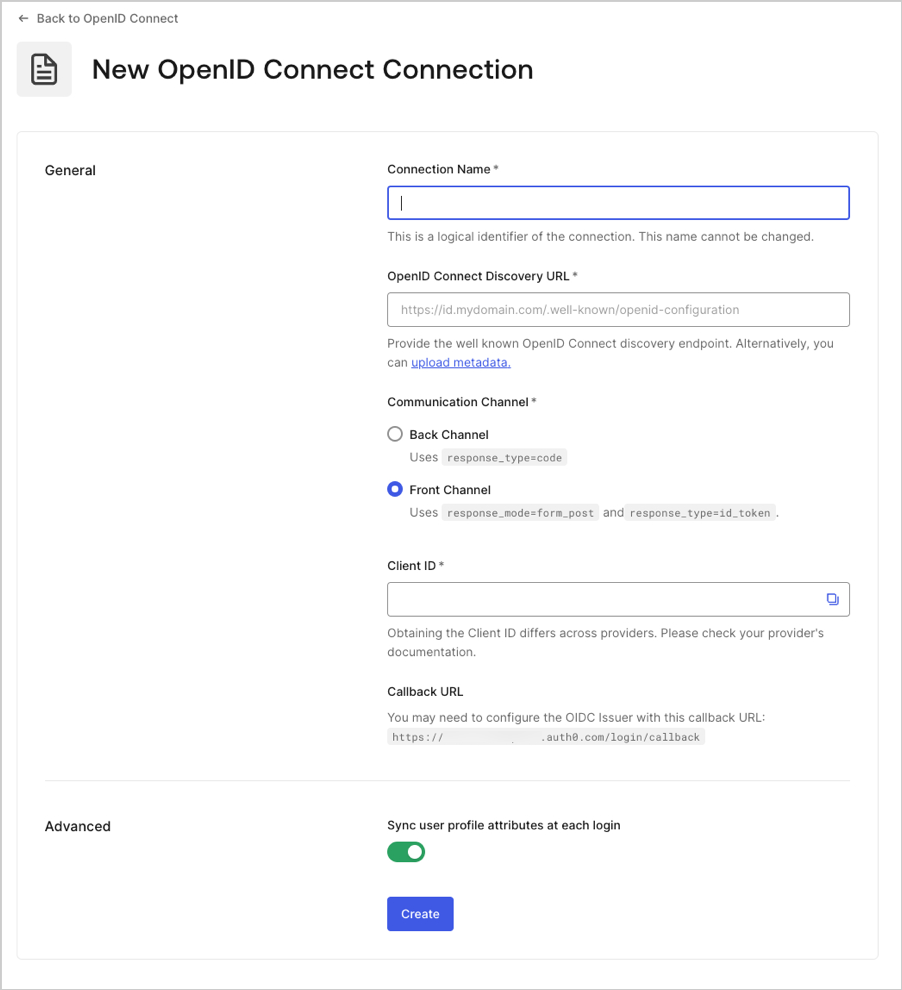
- Enter details for your connection, and select Create:
| Field | Description |
|---|---|
| Connection name | Logical identifier for your connection; it must be unique for your tenant. Once set, this name can’t be changed. |
| OpenID Connect Discovery URL | URL where Auth0 can find the well-known OpenID Connect discovery endpoint, usually available at the /.well-known/openid-configuration endpoint. You can enter the base URL or the full URL. You will see a green checkmark if it can be found at that location, a red mark if it cannot be found, or an error message if the file is found but the required information is not present in the configuration file. For more information, read Configure Applications with OIDC Discovery. |
| Communication Channel | Set to Front Channel or Back Channel. Front Channel uses the OIDC protocol with response_mode=form_post and response_type=id_token. Back Channel uses response_type=code. |
| Client ID | The identifier given to you by your provider. Unique identifier for your registered application. Enter the saved value of the Client ID for the app you registered with the OIDC Identity Provider. Each provider manages this step differently. |
| Client Secret | Available if Back Channel is chosen earlier. The secret given to you by your provider and each provider manages this step differently. |
| Callback URL | URL to which Auth0 redirects users after they authenticate. Ensure that this value is configured for the app you registered with the OIDC Identity Provider. |
| Sync user profile attributes at each login | If selected, your tenant updates the relevant name, nickname, given_name, family_name, or picture root attributes each time a user logs in. |
-
In the Settings view, make additional configuration adjustments, if necessary.
| Field | Description |
|---|---|
| Connection Name | The name you provided when you created this connection. It can’t be changed. |
| Connection Metadata | Automatically generated when by the Well-Known Endpoint URL you provided in the previous screen, this can be overwritten by uploading a new metadata file. |
| Communication Channel | Set to Front Channel or Back Channel. Front Channel uses the OIDC protocol with response_mode=form_post and response_type=id_token. Back Channel uses response_type=code. |
| Client ID | The identifier given to you by your provider. Each provider manages this step differently. |
| Client Secret | The secret given to you by your provider. Each provider manages this step differently. |
| Scopes | A comma-separated list of Auth0 scopes to request when connecting to the Identify Provider. This will affect the data stored in the user profile. You are required to include at least the openid scope. Note that the connection does not call /userinfo endpoint and expects the user claims to be present in the id_token. |
| Callback URL | Some providers need this URL to complete your OIDC connection. |
| User Mapping | Provides templates to map specific user attributes to connection variables. |
| Connection Profile | To understand how to change your connection profile, read Configure PKCE and Claim Mapping for OIDC Connections. |
- In the Provisioning view, configure how user profiles get created and updated in Auth0.
| Field | Description |
|---|---|
| Sync user profile attributes at each login | When enabled, Auth0 automatically syncs user profile data with each user login, thereby ensuring that changes made in the connection source are automatically updated in Auth0. |
| Sync user profiles using SCIM | When enabled, Auth0 allows user profile data to be synced using SCIM. For more information, see Configure Inbound SCIM. |
- In the Login Experience view, configure how users log in with this connection.
| Field | Description |
|---|---|
| Home Realm Discovery | Compares a user’s email domain with the provided identity provider domains. For more information, read Configure Identifier First Authentication |
| Display connection button | This option displays the following choices to customize your application’s connection button. |
| Button display name (Optional) | Text used to customize the login button for Universal Login. When set the button reads: “Continue with {Button display name}”. |
| Button logo URL (Optional) | URL of image used to customize the login button for Universal Login. When set, the Universal Login login button displays the image as a 20px by 20px square. |
Optional fields are available with Universal Login only. Customers using Classic Login will not see the Add button, Button display name, or Button logo URL.
- Select Save Changes.
Create an enterprise connection using the Management API
These examples will show you the variety of ways you can create the connection using Auth0’s . You ca configure the connection by either providing a metadata URI or by setting the OIDC URLs explicitly. For more information, read Identity Providers.Use front-channel with discovery endpoint
Use back-channel with discovery endpoint
Use back-channel specifying issuer settings
Use front-channel specifying issuer settings
Configure PKCE and claims mapping
This Enterprise connection can support Proof Key for Code Exchange (PKCE), as well as attribute and token mapping. To learn more, review Configure PKCE and Claim Mapping for OIDC Connections.Enable the enterprise connection for your Auth0 application
To use your new enterprise connection, you must first enable the connection for your Auth0 Applications.Test the connection
Now you’re ready to test your connection.Manually configure Issuer metadata
If you click Show Issuer Details on the Issuer URL endpoint, you can see the data and adjust it if you need to.Federate with Auth0
The Connect enterprise connection is useful when federating to another Auth0 tenant. Enter your Auth0 tenant URL (for example,https://<tenant>.us.auth0.com) in the Issuer field, and enter the Client ID for any application in the tenant to which you want to federate in the Client ID field.
New tenants will have
us as part of the URL. Tenants created before the regional domain addition will continue to work. For example, https://{YOUR ACCOUNT}.auth0.com.
